Security Risk Assessments and Management Assistance
At Connley Walker, our commitment to providing exceptional security consultancy extends to offering comprehensive security risk assessments and management assistance services. We understand that in today’s dynamic and interconnected world, organisations face an array of evolving security threats. Our team, comprised of highly experienced and certified professionals, brings a wealth of knowledge to the table. We delve into the intricacies of the ever-evolving security landscape, ensuring that our clients receive insights that go beyond conventional approaches.
Through a thorough and tailored approach, we collaborate with organisations to identify and mitigate potential security threats effectively. Our focus goes beyond mere risk identification; we strive to empower organisations by providing strategic guidance on security risk management. By leveraging our expertise, organisations not only fortify their defences but also establish a proactive stance against emerging security challenges. With Connley Walker, you gain a trusted partner dedicated to creating a secure environment, safeguarding assets, and prioritising the safety of your personnel.

What is a Security Risk Assessment?
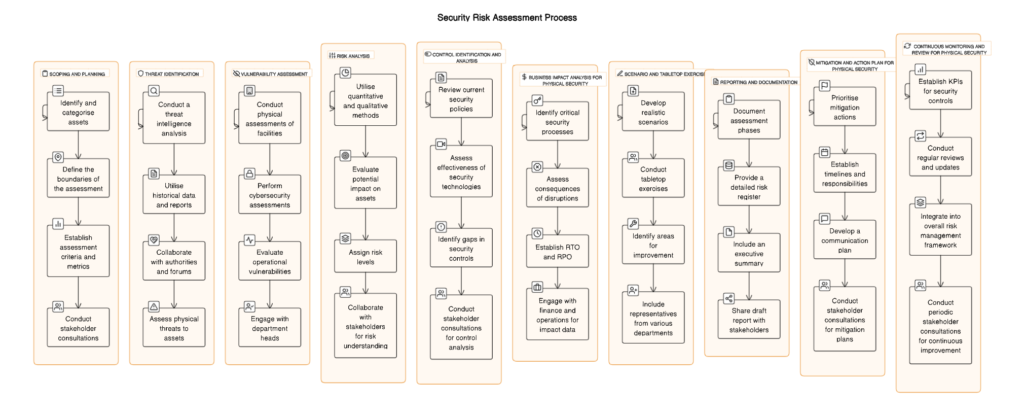
A Security Risk Assessment (SRA) is a comprehensive and systematic evaluation of potential risks, vulnerabilities, and threats to an organisation’s assets, operations, and personnel. It serves as a strategic tool to identify, analyse, and mitigate security risks, ensuring the robust protection of critical elements within an organisational environment.
Purpose of a Security Risk Assessment:
Risk Identification:
- Uncover and categorise potential security risks, including physical, cyber, and operational threats.
Vulnerability Analysis:
- Assess vulnerabilities within the organisation’s infrastructure, processes, and systems.
Threat Assessment:
- Evaluate the likelihood and impact of various threats, both internal and external.
Asset Protection:
- Safeguard key assets, including data, personnel, intellectual property, and physical infrastructure.
Key Components of a Security Risk Assessment:
Risk Analysis:
- Conduct a thorough analysis of identified risks, considering their potential impact and likelihood.
Physical Security Controls:
- Evaluate the effectiveness of physical security measures, such as access control systems, surveillance, and perimeter security.
Cybersecurity Evaluation:
- Assess the organisation’s cybersecurity posture, including network security, data protection, and incident response capabilities.
Operational Review:
- Examine operational processes and procedures to identify areas for improvement in security protocols.
Stakeholder Consultation:
- Engage with key stakeholders to gather insights, align security measures with organisational goals, and ensure comprehensive risk coverage.
Benefits of a Security Risk Assessment:
Proactive Risk Mitigation:
- Identify and address potential risks before they escalate, fostering proactive risk management.
Resource Allocation:
- Optimise resource allocation by prioritising security measures based on identified risks.
Regulatory Compliance:
- Ensure compliance with industry regulations and standards, mitigating legal and regulatory risks.
Continuous Improvement:
- Establish a framework for ongoing improvement, adapting security measures to evolving threats.
Organisational Resilience:
- Enhance the organisation’s resilience by fortifying its ability to withstand and recover from security incidents.
Conclusion:
In essence, a Security Risk Assessment is a cornerstone of effective security management, providing organisations with the insights needed to build a robust defence against a dynamic threat landscape. By systematically evaluating risks, implementing targeted security measures, and fostering a culture of continuous improvement, businesses can safeguard their assets, operations, and reputation with confidence.
Whether you are a large corporation, a government entity, or a small business, a Security Risk Assessment is a vital investment in the long-term security and success of your organisation.
Our Services
- Thorough Security Risk Assessments: Our team conducts in-depth security risk assessments to identify vulnerabilities, weaknesses, and potential threats within an organisation’s premises. Through a systematic approach, we evaluate physical security measures, access controls, surveillance systems, perimeter protection, and more. We also consider operational processes, personnel security, and information handling practices. By assessing these factors comprehensively, we provide clients with a detailed understanding of their security landscape.
- Risk Mitigation Strategies: Based on the findings of the security risk assessment, we develop practical and effective risk mitigation strategies. We work closely with our clients to implement tailored solutions that align with their specific requirements and objectives. Our recommendations encompass a range of measures, including technology upgrades, procedural improvements, and personnel training. We focus on achieving a balance between security measures and operational efficiency, ensuring optimal protection without hindering day-to-day operations.
- Security Policy and Procedure Development: Strong security policies and procedures form the backbone of an effective security management framework. We assist organisations in developing comprehensive policies and procedures that align with industry standards and regulatory requirements. Our expertise in security management ensures that these documents provide clear guidelines and instructions for staff, enabling them to understand and comply with security protocols.
- Ongoing Security Management Support: Security is not a one-time effort; it requires continuous monitoring and management. Our team provides ongoing support and assistance to help organisations maintain and enhance their security measures. We conduct periodic security reviews, evaluate the effectiveness of implemented measures, and recommend improvements as necessary. We also stay updated with the latest security trends and technologies to ensure our clients remain at the forefront of security practices.
Why Choose Connley Walker?
- Expertise and Experience: With years of experience in the industry, we have honed our skills and knowledge to deliver exceptional security risk assessment and management assistance. Our team of experts stays up-to-date with the latest security trends, best practices, and regulatory requirements, ensuring that our clients receive the highest quality service.
- Tailored Solutions: We understand that each organisation has unique security requirements. That’s why we take a customised approach to our services, tailoring our solutions to meet the specific needs and challenges of our clients. By considering factors such as industry, location, size, and operations, we provide solutions that are practical, effective, and aligned with our clients’ goals.
- Commitment to Client Satisfaction: At Connley Walker, client satisfaction is our top priority. We build strong partnerships with our clients, working collaboratively to address their security concerns and exceed their expectations. Our dedicated team is always available to provide guidance, answer questions, and offer ongoing support throughout the engagement.
When it comes to security risk assessments and management assistance, Connley Walker is your trusted partner. Contact us today to discuss your security needs and find out how we can help safeguard your organisation against potential threats.
Connley Walker is an independent group of licensed security consulting professionals specialising in both physical and cyber security, along with expertise in risk management. Connley Walker fully complies with the Australian Government’s Information Privacy Principles (IPP) and is able to provide IPP consulting services related to securing your information.
Trusted by Australia's leading organisations.

Contact Us
FIll out the form below and we will contact you as soon as possible

Connley Walker is an independent group of licensed security consulting professionals with engineers specialising in physical and cyber security and risk management.
Copyright ©2023 Connley Walker Holdings Pty Ltd. All Rights Reserved.
LICENCES AND REGISTRATIONS
ACT – Security Master Licence No. 17502533.
NSW – Security Master Licence No. 409109204.
NT – No licence required.
QLD – Security Firm Licence No. 3255594.
QLD – Registered Professional Engineers No. 21615.
SA – Exempt from a licence as Engineers (Security and Investigation Industry Regulations Part 2, 5 (1) (b)).
VIC – Registered Building Practitioners No. EE21166.
VIC – Private Security Business Registration No. 720-062-90S.
TAS – Building Service Provider Licence No. 363589169.
WA – Security Agent Licence No. SA56167.
CREDENTIALS AND AFFILIATIONS
ISO 9001:2015 Quality Assured.
SCEC Endorsed Security Zone Consultants (Registration Number 0075).
Pre-qualified consultants to the Victorian Government.
Pre-qualified consultants to the NSW Government.
Pre-qualified consultants to the NT Government.
Pre-qualified consultants to the Tasmanian Government.
Represent Engineers Australia on Australian Standards for Security.
Members of Australian Security Industry Association Limited (ASIAL).
Members of Australian Institute of Project Management (AIPM).
Members of Engineers Australia.
Federal Government Endorsed Suppliers.
CONTACT US
POSTAL ADDRESS:
16 Grey Street
Caulfield South, Victoria 3162
PHONE: